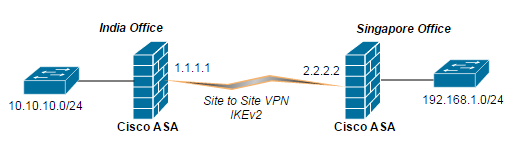
We are using the following topology, the most popular one. 2 sites in different geographical location and both have static IP address configured in their ASA firewall. Before we begin, you should also know the advantages of using IKEv2
- IKEv2 uses fewer messsages to establish tunnel thus saves bandwidth
- IKEv2 has built-in mechanism against DoS attacks. ASA uses minimum CPU until it validates the initiator.
- IKEv2 has built-in support for NAT traversal, EAP authentication, keep-alive mechanism (Dead peer detection)
In ASA of both sites
Phase 1: IKE policy
The configuration is very similar to IKEv1 but the only additional command is prf sha
IND-ASA(config)#crypto ikev2 policy 10 IND-ASA(config-ikev2-policy)#encryption aes-gcm-256 IND-ASA(config-ikev2-policy)#integrity sha512 sha384 sha256 IND-ASA(config)#crypto ikev2 enable outside
Even if we don’t configure certain parameters at initial configuration, Cisco ASA sets its default settings for dh group (2), prf (sha) and SA lifetime (86400 seconds). Let’s look at the ASA configuration again using sh run crypto ikev2 command.
IND-ASA(config)# sh run crypto ikev2 crypto ikev2 policy 10 encryption aes-gcm-256 integrity sha512 sha384 sha256 group 2 prf sha lifetime seconds 86400 crypto ikev2 enable outside
Phase 2: IPsec proposal
In IKEv1, we configure transform set and in IKEv2, its a ipsec-proposal.
crypto ipsec ikev2 ipsec-proposal AES-256-SHA-256 protocol esp encryption aes-256 protocol esp integrity sha-256
In ASA of India network
object-group network india_network network-object 10.10.10.0 255.255.255.0 object-group network singapore_network network-object 192.168.1.0 255.255.255.0 nat (inside,outside) source static india_network india_network destination static singapore_network singapore_network access-list ind_sin_acl extended permit ip object-group india_network object-group singapore_network
In crypto map, specify the access-list, peer ip address and IPsec proposal. Do not forget to enable the crypto map on the outside interface.
crypto map outside_map 5 match address ind_sin_acl crypto map outside_map 5 set peer 2.2.2.2 crypto map outside_map 5 set ikev2 ipsec-proposal IKEV2-IPSEC-ESP-AES-SHA1 crypto map outside_map interface outside
For IKEv2, asymmetric pre-shared keys can be configured. If you specify same pre-shared key for both local and remote, then you have configured legacy IKEv1 technology.
tunnel-group 2.2.2.2 type ipsec-l2l tunnel-group 2.2.2.2 ipsec-attributes ikev2 remote-authentication pre-shared-key itadminguide ikev2 local-authentication pre-shared-key cisco
In ASA of Singapore network
object-group network india_network network-object 10.10.10.0 255.255.255.0 object-group network singapore_network network-object 192.168.1.0 255.255.255.0 nat (inside,outside) source static singapore_network singapore_network destination static india_network india_network access-list sin_ind_acl extended permit ip object-group singapore_network object-group india_network crypto map outside_map 5 match address ind_sin_acl crypto map outside_map 5 set peer 1.1.1.1 crypto map outside_map 5 set ikev2 ipsec-proposal IKEV2-IPSEC-ESP-AES-SHA1 crypto map outside_map interface outside tunnel-group 1.1.1.1 type ipsec-l2l tunnel-group 1.1.1.1 ipsec-attributes ikev2 remote-authentication pre-shared-key cisco ikev2 local-authentication pre-shared-key itadminguide