In this guide, we are configuring IKEV1 VPN between Cisco ASA and Paloalto firewall. This is applicable to all models of Cisco and PA firewalls.
Configure Cisco ASA:
1) Phase 1: IKE policy
ciscoasa(config)# crypto ikev1 policy 10
ciscoasa(config-ikev1-policy)# authentication pre-share
ciscoasa(config-ikev1-policy)# encryption 3des
ciscoasa(config-ikev1-policy)# hash sha
ciscoasa(config-ikev1-policy)# group 2
ciscoasa(config-ikev1-policy)# lifetime 86400
ciscoasa(config)# crypto ikev1 enable outside
2) Phase 2: IPSec proposal
ciscoasa(config)# crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
3) Network Objects and ACL
ciscoasa(config)# object-group network india_network
ciscoasa(config-network-object)# network-object 10.10.10.0 255.255.255.0
ciscoasa(config)# object-group network singapore_network
ciscoasa(config-network-object)# network-object 192.168.1.0 255.255.255.0
ciscoasa(config)# nat (inside,outside) source static india_network india_network destination static singapore_network singapore_network
ciscoasa(config)# access-list ind_sin_acl extended permit ip object-group india_network object-group singapore_network
4) Cryptomap
ciscoasa(config)# crypto map outside_map 5 match address ind_sin_acl
ciscoasa(config)# crypto map outside_map 5 set peer 2.2.2.2
ciscoasa(config)# crypto map outside_map 5 set ikev1 transform-set ESP-3DES-MD5
ciscoasa(config)# crypto map outside_map 5 set pfs group2
ciscoasa(config)# crypto map outside_map interface outside
Defaults
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
5) Group Policy and Tunnel Interface
Create a Group policy for ikev1 vpn protocol and assign to tunnel interface.
ciscoasa(config)# group-policy GrpPolicy-2.2.2.2 internal
ciscoasa(config)# group-policy GrpPolicy-2.2.2.2 attributes
ciscoasa(config)# vpn-tunnel-protocol ikev1
ciscoasa(config)# tunnel-group 2.2.2.2 type ipsec-l2l
ciscoasa(config)# tunnel-group 2.2.2.2 ipsec-attributes
ciscoasa(config-tunnel-ipsec)# ikev1 pre-shared-key cisco
ciscoasa(config)# tunnel-group 2.2.2.2 general-attributes
ciscoasa(config)# default-group-policy GrpPolicy-2.2.2.2
Configure Paloalto Firewall:
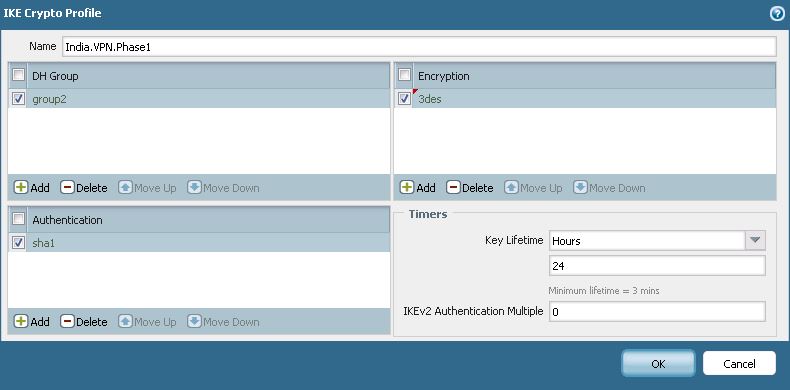
1) Phase 1: IKE Profile. Navigate to Network > Network Profiles > IKE Crypto
PA considers 86400 seconds lifetime to be too large and doesn’t accept. 86400 seconds is equivalent to 24 hours, hence I specified lifetime as 24 hours in PA firewall.
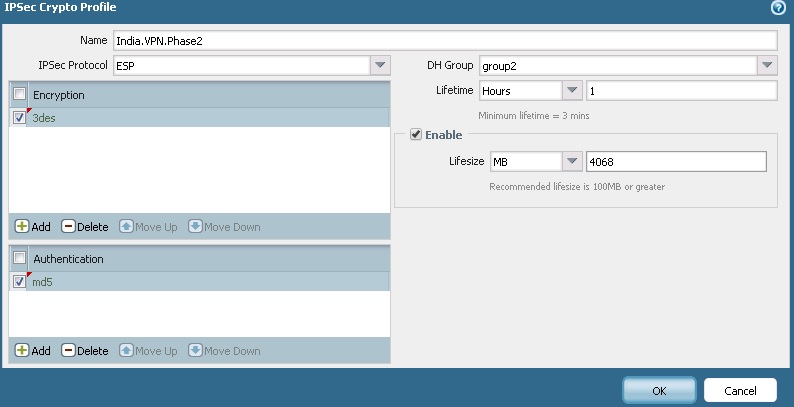
2) Phase 2: IPSec Profile. Navigate to Network > Network Profiles> IPSec Crypto
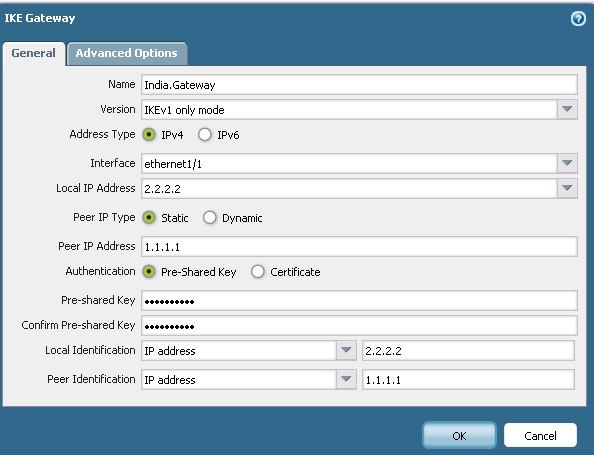
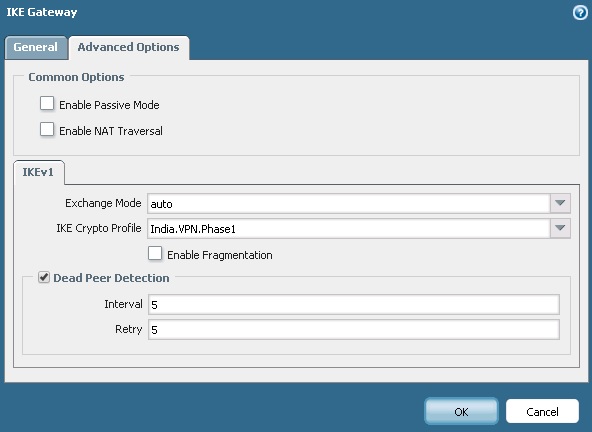
3) IPSec Gateway. Navigate to Network > Network Profiles> IKE Gateway
Specify the same pre-shared key used in Cisco firewall, in this example it is cisco
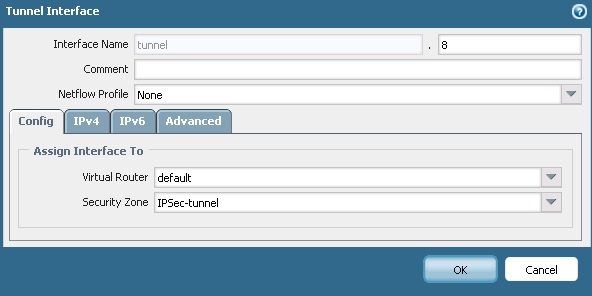
4) Tunnel Interface: Navigate to Network > Interfaces > Tunnel
Considering that you already created a separate zone for IPSec traffic and named as IPSec-tunnel.
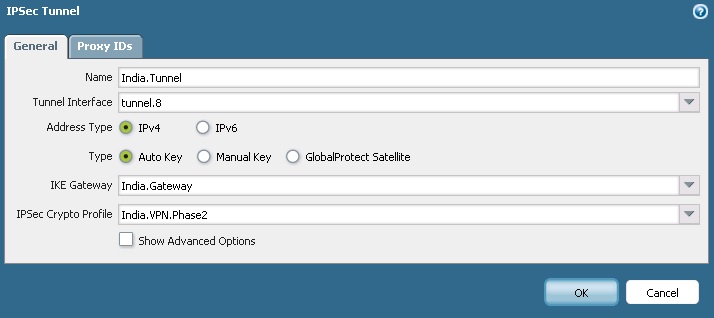
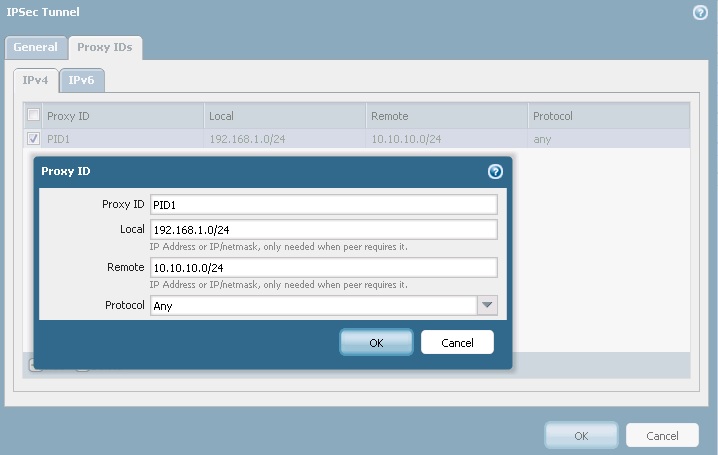
5) IPSec Tunnel: Navigate to Network > IPSec Tunnels
6) Security Policy. Navigate to Policies > Security
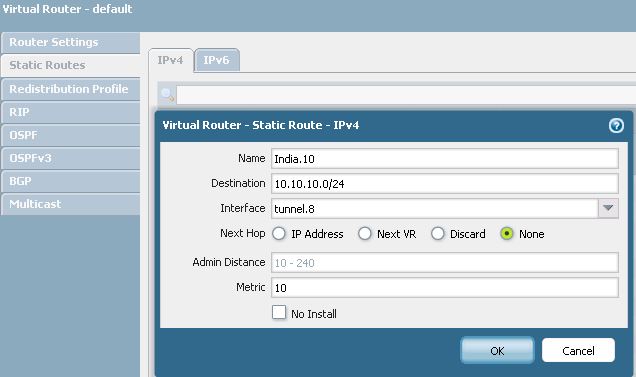
7) Virtual Router. Navigate to Network > Virtual Routers
To configure route, choose the Virtual Router specified in Step 4, in this example its default virtual router.
8) IKE Outside Interface. Navigate to Policies > Security
Finally, you need to open IKE (port 500) on outside interface for peer IP to establish IPSec Tunnel.