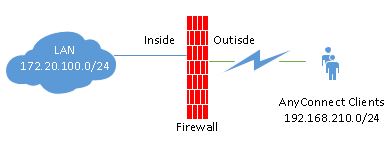
1.Create Network Objects
(config)# object network office-subnet subnet 172.20.100.0 255.255.255.0
(config)# object network anyconnect-subnet subnet 192.168.210.0 255.255.255.0
2.Create DHCP Pool for Anyconnect client
(config)# ip local pool anyconnect-pool 192.168.210.50-192.168.210.200 mask 255.255.255.0
3.Create ACL and NAT
(config)# access-list InternalHosts-SplitTunnelAcl standard permit 172.20.100.0 255.255.255.0
(config)# nat (inside,outside) source static office-subnet office-subnet destination static anyconnect-subnet anyconnect-subnet
4.Enable AnyConnect. Update your relevant image package.
(config)# webvpn
(config-webvpn)# enable outside
(config-webvpn)# anyconnect enable
(config-webvpn)# anyconnect image disk0:/anyconnect-win-4.2.05015-k9.pkg
5.Enable Login dropdown
(config)# webvpn
(config-webvpn)# tunnel-group-list enable
(config-webvpn)# no error-recovery disable
6.Configure Group Policy
(config)# group-policy GroupPolicy-VPN internal
(config)# group-policy GroupPolicy-VPN attributes
(config-group-policy)# wins-server none
(config-group-policy)# dns-server value 8.8.8.8 8.8.4.4
(config-group-policy)# vpn-tunnel-protocol ikev2 ssl-client
(config-group-policy)# split-tunnel-policy tunnelspecified
(config-group-policy)# split-tunnel-network-list value InternalHosts-SplitTunnelAcl
(config-group-policy)# default-domain value itadminguide.com
7.LDAP Authentication for VPN users:
aaa-server LDAPSRV protocol ldap
aaa-server LDAPSRV (inside) host 172.20.100.10
ldap-base-dn dc=itadminguide,dc=com
ldap-scope subtree
ldap-naming-attribute sAMAccountName
ldap-login-password *****
ldap-login-dn [email protected]
ldap-over-ssl enable
server-type microsoft
ldap-attribute-map map-anyconnect-login
ldap attribute-map map-anyconnect-login
map-name memberOf Group-Policy
map-value memberOf “CN=GS_VPN_Users,OU=GS_Group,DC=itadminguide,DC=com” GroupPolicy-VPN
8.Tunnel
(config)# tunnel-group Tunnel-VPN type remote-access
(config)# tunnel-group Tunnel-VPN general-attributes
(config-tunnel-general)# address-pool anyconnect-pool
(config-tunnel-general)# authentication-server-group LDAPSRV
(config-tunnel-general)# default-group-policy GroupPolicy-VPN
(config-tunnel-general)# tunnel-group Tunnel-VPN webvpn-attributes
(config-tunnel-webvpn)# group-alias Tunnel-VPN enable
Troubleshooting
| Commands | Description |
|---|---|
| #show vpn-sessiondb webvpn | Show current WebVPN sessions |
| #vpn-sessiondb logoff name | Disconnect a specific user from SSL or any other VPN session |